Bonjour,
depuis 2 jours je reçois des mails provenant de DNSSEC-DANE-Deployment-Statistics qui me signale que mon serveur de mail n’est pas valide DANE - cela depuis (je pense) que j’ai fait des tests de bonne configuration d’email depuis le siteweb https://internet.nl - en fait je crois que cela vient de mon register de domaine gandi.net 
De : DANE Survey Notices <maillll@dnssec-stats.ant.isi.edu>
Pour : 7331b9..........39736938@contact.gandi.net
Copie à : hostmaster@lab3w.fr (moi)
Sujet : [Reminder] smtp.zw3b.eu[158.69.126.137], smtp.zw3b.net[2607:5300:60:9389:17:4c1:0:1a]: SMTP server DNS (DANE TLSA record) issue
çà pète, en passant 
CF : https://stats.dnssec-tools.org/explore/?zw3b.eu
Par contre j’ai l’impression qu’il y a un bug de vérification DANE ; on dirait que le site vérifie le port _443._tcp sur le nom SMTP (c’est un peu c** c**) 
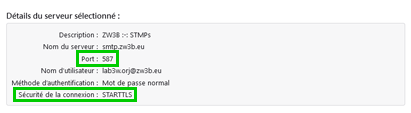
J’ai un serveur mail « mail.zw3b.eu ».
Le protocol SMTP (25) & SMTPs (465) & SMTPs STARTLS (587) (donc) sont valident DANE.
$ dig TLSA _25._tcp.smtp.zw3b.eu @dns.google +short
3 0 1 6A42E98D3EADBB58C37A4127CEF3BB8BD004AC8DA39EE14F46549E52 C75F1C4F
$ dig TLSA _465._tcp.smtp.zw3b.eu @dns.google +short
3 0 1 6A42E98D3EADBB58C37A4127CEF3BB8BD004AC8DA39EE14F46549E52 C75F1C4F
$ dig TLSA _587._tcp.smtp.zw3b.eu @dns.google +short
3 0 1 6A42E98D3EADBB58C37A4127CEF3BB8BD004AC8DA39EE14F46549E52 C75F1C4F
Le webmail HTTPs (TLS) (donc) valide DANE.
$ dig TLSA _443._tcp.webmail.zw3b.eu @dns.google +short
3 0 1 6A42E98D3EADBB58C37A4127CEF3BB8BD004AC8DA39EE14F46549E52 C75F1C4F
Est-ce la bonne configuration ?
Il me semble bien - n’est-ce pas ?
Je pourrais ajouter un enregistrement DNS pour cette question (mais je ne vois pas à quoi çà sert) :
$ dig TLSA _443._tcp.smtp.zw3b.eu @dns.google +short
Merci pour vos réponses.
Salutations,
Romain
J’ajoute çà :
Sur le service « webmail.zw3b.eu:443 » :
$ echo | openssl s_client -showcerts -servername webmail.zw3b.eu -connect webmail.zw3b.eu:443 2>/dev/null | openssl x509 -inform pem -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
04:03:b6:45:1d:b1:5f:11:2e:8c:ac:d0:af:9c:15:e9:67:fe
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = US, O = Let's Encrypt, CN = R3
Validity
Not Before: Nov 7 15:26:37 2023 GMT
Not After : Feb 5 15:26:36 2024 GMT
Subject: CN = mail.zw3b.eu
Subject Public Key Info:
Public Key Algorithm: id-ecPublicKey
Public-Key: (384 bit)
pub:
04:12:c1:14:2c:d2:45:d6:92:82:10:b5:27:58:3d:
d2:10:80:40:2d:a4:07:b5:6e:2f:9c:91:72:cb:cd:
a3:1e:09:ec:75:08:f5:41:37:0c:9e:0d:a6:fe:89:
e5:41:3f:77:48:54:a6:35:15:4f:95:b9:82:c9:42:
8e:f6:ff:cd:f4:3a:be:77:3f:af:d4:04:40:a0:33:
cf:65:15:52:30:e4:ea:e3:0a:72:9b:6a:41:1a:54:
9a:bd:52:ee:6b:d4:ec
ASN1 OID: secp384r1
NIST CURVE: P-384
X509v3 extensions:
X509v3 Key Usage: critical
Digital Signature
X509v3 Extended Key Usage:
TLS Web Server Authentication, TLS Web Client Authentication
X509v3 Basic Constraints: critical
CA:FALSE
X509v3 Subject Key Identifier:
FF:D3:55:B5:EB:0C:84:A0:8B:A7:3C:04:38:73:8F:02:9D:C1:9E:8D
X509v3 Authority Key Identifier:
keyid:14:2E:B3:17:B7:58:56:CB:AE:50:09:40:E6:1F:AF:9D:8B:14:C2:C6
Authority Information Access:
OCSP - URI:http://r3.o.lencr.org
CA Issuers - URI:http://r3.i.lencr.org/
X509v3 Subject Alternative Name:
DNS:imap.zw3b.blog, DNS:imap.zw3b.com, DNS:imap.zw3b.eu, DNS:imap.zw3b.fr, DNS:imap.zw3b.net, DNS:imap.zw3b.site, DNS:imap.zw3b.tv, DNS:mail.zw3b.blog, DNS:mail.zw3b.com, DNS:mail.zw3b.eu, DNS:mail.zw3b.fr, DNS:mail.zw3b.net, DNS:mail.zw3b.site, DNS:mail.zw3b.tv, DNS:pop.zw3b.blog, DNS:pop.zw3b.com, DNS:pop.zw3b.eu, DNS:pop.zw3b.fr, DNS:pop.zw3b.net, DNS:pop.zw3b.site, DNS:pop.zw3b.tv, DNS:smtp.zw3b.blog, DNS:smtp.zw3b.com, DNS:smtp.zw3b.eu, DNS:smtp.zw3b.fr, DNS:smtp.zw3b.net, DNS:smtp.zw3b.site, DNS:smtp.zw3b.tv, DNS:webmail.zw3b.blog, DNS:webmail.zw3b.com, DNS:webmail.zw3b.eu, DNS:webmail.zw3b.fr, DNS:webmail.zw3b.net, DNS:webmail.zw3b.site, DNS:webmail.zw3b.tv
X509v3 Certificate Policies:
Policy: 2.23.140.1.2.1
CT Precertificate SCTs:
Signed Certificate Timestamp:
Version : v1 (0x0)
Log ID : 3B:53:77:75:3E:2D:B9:80:4E:8B:30:5B:06:FE:40:3B:
67:D8:4F:C3:F4:C7:BD:00:0D:2D:72:6F:E1:FA:D4:17
Timestamp : Nov 7 16:26:38.263 2023 GMT
Extensions: none
Signature : ecdsa-with-SHA256
30:45:02:21:00:94:67:2C:65:F1:F5:7F:18:4B:D8:A5:
78:67:B1:D3:83:8B:E3:0F:4E:0B:86:02:DE:B8:42:95:
55:6E:1D:70:0F:02:20:37:25:80:CE:A2:82:CD:BF:C8:
DC:4B:FB:75:BA:B7:89:A6:7C:2D:36:B5:8B:C9:7F:45:
30:B0:6C:F6:6C:2A:52
Signed Certificate Timestamp:
Version : v1 (0x0)
Log ID : EE:CD:D0:64:D5:DB:1A:CE:C5:5C:B7:9D:B4:CD:13:A2:
32:87:46:7C:BC:EC:DE:C3:51:48:59:46:71:1F:B5:9B
Timestamp : Nov 7 16:26:38.323 2023 GMT
Extensions: none
Signature : ecdsa-with-SHA256
30:46:02:21:00:CD:35:50:C5:E3:D5:DF:4C:D5:C0:A6:
D0:B8:34:2F:74:32:28:7C:24:49:E8:A0:8E:4B:97:02:
C0:10:47:EB:BC:02:21:00:8A:28:D3:A3:34:CE:25:B6:
54:34:E7:28:AF:BC:54:86:7A:B9:F8:53:20:BE:03:68:
55:8B:56:55:84:F8:D7:38
Signature Algorithm: sha256WithRSAEncryption
33:5f:6c:4b:6e:b5:de:5c:bc:5a:62:f4:93:7f:cc:c7:aa:4e:
41:f1:b9:d6:48:58:ec:d9:8f:d8:66:26:f1:d0:5a:9e:3a:0c:
35:bf:9c:9a:74:53:fe:b1:1a:32:a8:65:15:74:04:49:da:68:
1e:db:ff:84:3e:58:14:f0:71:8e:25:1d:45:1e:28:3f:ea:17:
16:4f:0b:51:04:c0:5d:c4:94:72:73:10:5f:4c:a8:4a:1a:a6:
84:31:fa:b1:3b:f3:69:50:79:74:4b:0d:ca:6a:11:82:1f:bf:
26:be:d7:35:3d:f1:ae:67:e8:c6:a5:56:21:36:7c:07:46:96:
8e:83:b5:9d:27:16:ae:68:2e:48:94:57:f3:b0:ff:fe:f6:81:
e6:c7:91:3c:36:5c:69:ac:02:0d:00:4b:e0:3c:9b:bf:2f:41:
85:a8:c1:26:2c:6a:f5:fd:d3:06:02:b7:89:84:76:65:a9:22:
88:67:1a:98:ee:8b:25:74:54:c5:4a:15:45:0f:7d:32:9f:d8:
10:de:42:44:25:3d:65:1d:9d:98:f5:5b:b4:4e:08:44:ba:4c:
1e:02:52:ff:c8:55:ba:f5:0c:8e:8c:d4:4a:e3:da:a0:1d:b4:
b4:fb:13:2a:4c:2f:11:40:5c:02:81:e6:ec:2b:d2:66:1f:d2:
68:a1:c1:0b
Sur le service « smtp.zw3b.eu:25 » :
$ echo | openssl s_client -showcerts -servername smtp.zw3b.eu -connect smtp.zw3b.eu:25 -6 2>/dev/null | openssl x509 -inform pem -noout -text
unable to load certificate
140013873140928:error:0909006C:PEM routines:get_name:no start line:../crypto/pem/pem_lib.c:745:Expecting: TRUSTED CERTIFICATE
?
Aurais-je fais une bourde (pourtant j’arrive normalement à m’authentifier avec mon logiciel de mails Mozilla Thunderbird à recevoir et send)…
J’ai pû lire que par exemple les signatures DKIM peuvent être au maximum en ec-256 plutôt ed25519-sha256 et non pas en ec-384 mais je ne crois pas ce soit la même chose pour le protocol SMTP.
Je ne sais pas exactement.
Pour DKIM :
- Algorithm RSA-SHA256 (rfc6376 : DomainKeys Identified Mail (DKIM) Signatures)
- Algorithm Ed25519-SHA256 : (rfc8463 : A New Cryptographic Signature Method for DomainKeys Identified Mail (DKIM))
Pour SMTP - je check çà …
Je lis « liste d’algorithmes de chiffrement pour la négociation TLS a été mise à jour en janvier 2021. » sur cette page : Algorithmes de chiffrement pour les connexions TLS SMTP…
TLS 1.3
- TLS_AES_128_GCM_SHA256
- TLS_AES_256_GCM_SHA384
- TLS_CHACHA20_POLY1305_SHA256